A recent survey, along with an OCR statement, reiterate the importance of organizations understanding healthcare application security measures.
As more covered entities and business associates continue to implement mobile options, healthcare application security is an increasingly critical aspect to overall data security.
From www.healthiit.security.com launched inn time during the ADA
Nyhetsinfo
www red DiabetologNytt
If a recent survey is any indication, organizations should take particular care when it comes to cloud-based applications, as over one-quarter of such apps were found to be risky.
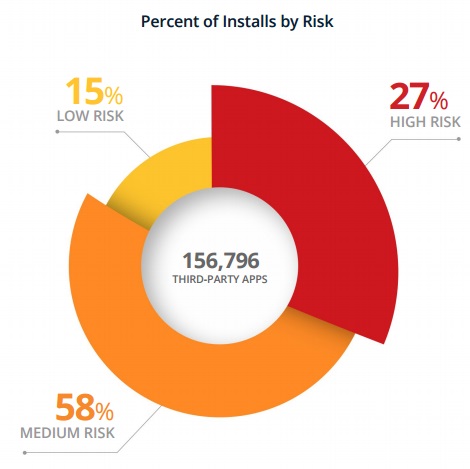
CloudLock’s Q2 2016 Cloud Cybersecurity Report found that 27 percent of third-party apps are classified as high risk.
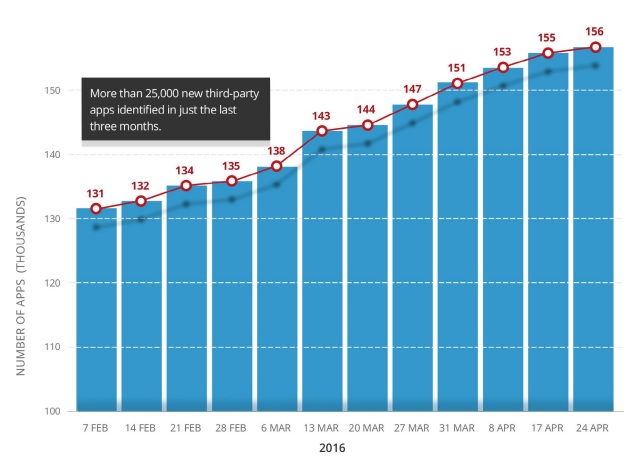
There has also been a huge increase in apps from 2014 to 2016, growing from 5,500 to nearly 160,000 in that time frame.
There is a real danger in Shadow IT, according to the report summary, which is when employees utilize applications without IT approval.
“As more and more organizations adopt cloud platforms, new Shadow IT risk vectors are coming into play in the form of connected third-party apps,” the report’s authors explained. “These apps are authorized using corporate credentials, demand extensive permission sets, and communicate with corporate SaaS platforms via OAuth connections.”
For the survey, application risk was measured across access scopes, community trust ratings, and application threat intelligence.
Of all the apps granted access to corporate systems in 2016, 27 percent were classified as high risk by security teams, while 58 percent were listed as medium-risk and just 15 percent were low-risk.
As previously mentioned, the number of third-party apps has greatly increased in recent years. Since 2014, the number of third-party application installations has increased 11 times, while there has been a 19 percent increase in the last three months alone, according to the report.
“Over the past two years, the number of apps per average organization has increased from 130 to 733,” wrote the report’s authors. “There are even organizations with more than 18,500 applications, all with the potential to become backdoors through which hackers can easily infiltrate their environments.”
In terms of healthcare application security, the report found that 28 percent of third-party apps utilized by healthcare providers were deemed high-risk by IT teams. Fifty-six percent were listed as medium-risk, while just 16 percent were considered low-risk apps.
The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) is also taking note of potential third-party application risk, releasing a document on how organizations should review their apps.
Third-party application software is designed to work within operating systems, OCR explained, as well as help users complete tasks on computers and other devices. However, recent research shows that while a majority of companies use third-party applications or software, less than 1 in 5 organizations has performed third-party software verification.
“Covered Entities and Business Associates should define the criteria they are willing to accept for safe third-party applications, including open source and public domain applications,” OCR urged. “Applications should meet the corporate standards set by the entities and also satisfy compliance requirements, and entities should test against these criteria.”
Healthcare organizations should also install the necessary software patches or the most updated version of an app, the statement warned. Even so, these patches should be assessed before deployment to ensure they do not inadvertently put a system at risk.
Finally, OCR encouraged organizations to review any software license agreements, which can also be referred to as an end-user license agreement (EULA). OCR specifically cited recommendations from the United States Computer Emergency Readiness Team (US-CERT).
“Software license agreements are legal binding agreements that can have restrictions on how the software can be used; the agreements can require entities to agree to certain conditions when using the software, and can also limit their ability to sue for damages,” OCR stated.
According to US-CERT, facilities should review the software EULA before installing any software. Additionally, organizations need to be aware of any firewall prompts when they are installing software, as it should be verified that the software requires changes to your firewall settings for normal operation.
It will also be beneficial for organizations to familiarize themselves with a company, and review that company’s EULA “with added scrutiny.”
Dig Deeper:
